This is a writeup for the challenge Phasestream 1, part of the Hack the box's Cyberapocalypse CTF 2021, category Crypto.
Phasestream 1
In the first challenge, we're given a hex code, and the knowledge that it's been encoded using XOR with a 5-byte long key.
The top information here, is the length of the key. Since we expect to see a flag pop out of this encoded value, we know that it will start with CHTB{, which is exactly 5 bytes long.
And since the XOR operation is its own inverse, we know that if we apply a XOR operation on the encoded value using our known result CHTB{ as "key", we will get the original key as output.
We can simply use an online tool for this:
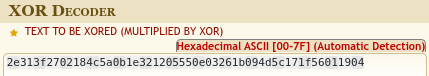
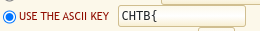

We get our key to be mykey!
We could also do this using this tool to do the same, since we can supply a key to it to decode. But we need to supply it with an ASCII representation of the encoded result.
- Decode the hex of the encrypted flag into ASCII
echo 2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904 | xxd -r -ps > encodedascii.txt
- Find the key by supplying the encrypted flag to
xor-decrypt, andCHTB{as key
python3 xor-decrypt.py -i "encodedascii.txt" -o key.txt -k CHTB{ -d
So we get mykey[IeqZQu@nOK6_KzZL, and deduce that mykey is the 5-byte key
- Decrypt the encrypted flag using our key
python3 xor-decrypt.py -i encodedascii.txt -o flag.txt -k mykey -d
And so, our flag finally is
CHTB{u51ng_kn0wn_pl41nt3xt}
Thank you for reading!
The information in this blog, as well as all the tools, apps and libraries I develop are currently open source.
I would love to keep it this way, and you can help!
You can buy me a coffee from here, which will go towards the next all-nighter I pull off!

Or you can support me and my code monthly over at Github Sponsors!
Thanks!
